5 Tips for Successful IoT Development

IoT development is more than just connected devices and networks. It is also about setting up an application architecture in such a way that promotes the smooth collection, processing, and storage of meaningful data.
And while doing all this, you have to make sure to create an efficient gateway so that crucial data doesn’t slip through the cracks and you just leave with unreliable information.
For startups and SMBs, IoT development has more risks, simply because they have to put up with the pressure of making everything right in the first attempt, as every mistake can prove to be very expensive for them.
While IoT has been acting as a boon for businesses in harnessing data power, the major challenge standing in front of them is ensuring performance consistency.
A professional IoT development company always keeps these things in mind. It knows these issues occur because companies ignore two crucial requirements during IoT development. These are:
- Monitoring and Performance Strategies: Most of the time companies miss out on creating effective strategies to ensure sound application delivery and continued digital experience.
- Scalability: No matter what business belongs to and how advanced is the technology you are using; new trends will demand you to change your existing practices. Ignoring scalability could prove dreadful for IoT development companies and enterprises and startups alike.
When building an application, it is crucial for the IoT Development Company to focus on creating robust application architecture and also work on planning scalability, monitoring, and performance strategies.
And so, you must know and use the below 5 IoT Development tips for startups and enterprises when building an Internet of Things (IoT) application.
Emphasize Human-Centric Design
Building a successful IoT solution requires a methodology that sets aside personal biases and focuses on insights revealed through a process. One such methodology is a four-step IoT development process rooted in human-centered design (HCD).
Image source:- Twisthink.com
However, simply following a methodology is not enough for guaranteed success. The way each step is interpreted and applied becomes critical. Here are five key elements to unlock IoT success:
Assemble your dream team
Best IoT projects should involve a diverse team comprising engineers, developers, designers, strategists, sales teams, project managers, and marketers. Convergent and divergent thinking from different perspectives pushes the team toward innovative possibilities.
Visual brilliance
Use visual storytelling to communicate the IoT solution effectively. Visualization sparks the imagination, enables stakeholders to question assumptions, and brings clarity to the project in ways that words alone cannot.
Stakeholder insights
Understanding the target audience and stakeholders’ wants, desires, and pain points can be the best IoT strategy. Stakeholder insights are crucial in building a successful solution. Engage with stakeholders throughout the development process to gather valuable insights.
Creative boldness
Instead of replicating what competitors have already built, leverage stakeholder learning to develop a unique solution that addresses unmet needs. Creative confidence is essential to pursue groundbreaking ideas that haven’t been explored before.
Adaptive Attitude
Be prepared for unexpected challenges, feedback, and setbacks. Stay open-minded and adaptable, avoiding the temptation to force ideas that don’t align with desired outcomes. Embrace a willingness to explore new possibilities and ask “what if” questions.
Adopting a methodology alone is not enough. Companies should embrace a human-centered design approach that deeply understands end-users’ needs. By recognizing and incorporating human-centered design methodologies, companies can create IoT solutions that truly resonate with users and lead to successful connections.
Implement Privacy by Design
Privacy by Design is a fundamental principle emphasizing integrating privacy and data protection for successful IoT development. By embedding privacy features and protocols into their solution’s design, architecture, and infrastructure, companies prioritize privacy from the outset. This approach establishes trust with users, ensures compliance with data regulations, and mitigates the risks of data breaches or unauthorized access.
Apple Inc is a notable example of a company that has implemented Privacy by Design. Apple has made privacy a key differentiator with its range of products and services. They have integrated privacy features into their devices, operating systems, and apps, providing users with enhanced control over their data.
Apple’s iOS, the operating system for iPhones and iPads, includes privacy-focused features like App Tracking Transparency, which requires user consent before apps can track their activity across other apps and websites. Additionally, Apple devices employ hardware-based security measures, such as Face ID and Touch ID, to safeguard user data.
Apple’s commitment to privacy is further exemplified through its app review process, where they scrutinize apps for potential privacy violations before allowing them on their App Store. They also require developers to provide clear privacy policies and obtain user consent for data collection.
By prioritizing privacy by design, Apple has gained a reputation for protecting user privacy and security. This has contributed to their success in building a loyal customer base and maintaining their market position.
Overall, Apple’s implementation of Privacy by Design showcases the importance of integrating privacy features and protocols into the development process. By following their example, organizations can establish trust, comply with regulations, and protect user data, ultimately enhancing their reputation and fostering user loyalty.
So now let’s take a closer look at tips for IoT development to implement privacy by design
Data minimization
Practice data minimization by only collecting and storing the necessary data for the intended purpose. Avoid collecting excessive or irrelevant data that may pose privacy risks. By minimizing data collection, you reduce the potential impact of a data breach and enhance user privacy.
Anonymization and pseudonymization
Implement techniques such as anonymization and pseudonymization to protect user identities. Anonymization removes personally identifiable information (PII) from datasets, while pseudonymization replaces identifiable data with pseudonyms. These techniques help protect user privacy while still allowing for data analysis and insights.
Secure authentication and access control
Implement robust authentication mechanisms to ensure only authorized individuals and devices can access the IoT application and its data. For example, utilize strong passwords, two-factor authentication, or biometric authentication methods like fingerprint or facial recognition to enhance security and prevent unauthorized access.
Regular security assessments
Conduct regular security assessments, penetration testing, and vulnerability scanning to identify and address any security loopholes or weaknesses in the IoT application. Stay updated on the latest security practices and promptly address any identified vulnerabilities to maintain user data’s integrity and privacy.
Transparent privacy policies
Develop clear and concise privacy policies that outline how user data is collected, stored, used, and shared within the IoT application. Ensure that these policies are easily accessible to users and written in plain language to enhance transparency and enable users to make informed decisions about their privacy.
User consent and control
Prioritize obtaining informed user consent for data collection and processing activities. Provide users with granular control over their privacy settings, allowing them to opt in or out of specific data sharing or processing activities. Make it easy for users to modify their consent preferences and provide clear instructions on how to do so.
Incident Response and Data Breach Management
Develop a comprehensive incident response plan to effectively handle data breaches or privacy incidents. This includes establishing protocols for detecting, containing, and mitigating the impact of a breach. Promptly notify affected users and regulatory authorities as required by applicable data protection regulations.
Careful Planning of the Functions
When developing IoT applications, careful planning of functions is crucial for user engagement and generating meaningful data. Before starting the IoT development process, you should have two key aspects: the desired user actions and the method by which these actions can provide valuable data insights.
Incorporating innovative mobile application development services into the planning phase of IoT development is essential for maximizing user engagement and data generation. These services enable businesses to leverage the expertise of professionals who specialize in creating mobile applications that align with user expectations and industry best practices.
The first level of planning involves determining the specific actions you want users to perform with your application. This could include tasks such as controlling devices, monitoring environmental conditions, or accessing information. It is essential to strike a balance between offering useful functionality and keeping the user interface intuitive and straightforward. Complex functions can overwhelm users and discourage their continued engagement. On the other hand, a well-designed user experience increases the likelihood of user adoption and regular usage.
The second level of planning focuses on how these functions can generate data that is valuable for gaining insights into user preferences and behavior. The data collected can be analyzed to improve the application’s features, tailor recommendations, and deliver personalized experiences. Organizations can make data-driven decisions to enhance their products and services by understanding user behavior patterns and preferences.
A study by Accenture revealed offering personalized experiences will translate to higher sales if businesses remove unintended barriers consumers report. Therefore, personalized experiences are key to driving higher sales and fostering customer loyalty in IoT development. By removing barriers reported by consumers, businesses can unlock success.
Selecting Communication Channel
When selecting a communication channel for your IoT application, it is essential to choose an advanced medium compatible with the IoT devices involved.
Now you must be pondering why it’s important. So the significance of selecting the right communication channel for IoT applications becomes evident when we look at the statistics. According to a report by IoT Analytics, the global number of IoT connections experienced a significant 18% growth in 2022, reaching a staggering 14.3 billion active IoT endpoints. This indicates the widespread adoption and integration of IoT devices in various industries.
Looking ahead, the projections for 2023 show an additional 16% increase, bringing the total number of active endpoints to 16.7 billion. This exponential growth emphasizes the need for a well-defined IoT strategy that encompasses an effective communication channel selection.
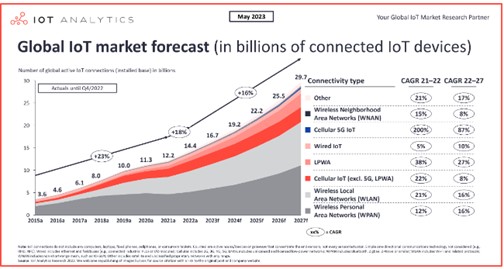
Image source:- iot-analytics.com
Let’s consider the following points when selecting a communication channel for your IoT application:
Range
Determine the distance over which your IoT devices need to communicate. Select a communication channel that can adequately cover the required range. For example, if you have devices spread across a large area, you may need a communication channel with a long-range capability, such as cellular networks or LPWAN (Low Power Wide Area Network).
Latency
Assess the real-time requirements of your IoT application. If you need quick response times, choose a communication channel with low latency, such as Wi-Fi or Bluetooth. On the other hand, if your application can tolerate some delays, technologies like Zigbee or Z-Wave may be suitable.
Bandwidth
Evaluate the data transfer requirements of your IoT devices. If your application involves high volumes of data, opt for communication channels with high bandwidth capacity, such as broadband internet or Ethernet. However, if your devices primarily transmit small amounts of data, low-bandwidth options like LoRaWAN or Sigfox may be sufficient.
Radio Signal Frequency
Determine the frequency range that your IoT devices support. Different regions and countries have regulations regarding radio frequencies, so ensure that the communication channel you choose aligns with the supported frequencies of your devices. Common frequency bands include 2.4 GHz and 5 GHz for Wi-Fi, as well as various frequency bands for cellular networks.
Signal Strength
Consider the signal strength requirements based on the environment in which your IoT devices operate. If your devices are deployed in challenging environments with obstacles or long distances, select a communication channel with strong signal penetration capabilities, such as cellular networks.
Security
Prioritize the security of your IoT application. Look for communication channels that offer encryption, authentication, and other security mechanisms to protect your data from unauthorized access and potential cyber threats.
Also Read – Top IoT Development Trends
Understand the core of IoT Application Architecture
Before diving into IoT application development, it’s important to understand and analyze the connected object. This involves exploring its capabilities to generate valuable data, which holds the key to unlocking meaningful insights.
In the domain of IoT, it is vital to focus on the object itself, seeking clarity on the required sensors and the specific information that is desired from it. This initial phase establishes the foundation for the entire architecture, enabling the seamless integration of the object into the IoT ecosystem.
The process begins by thoroughly examining the object’s unique characteristics and functionalities. What kind of data can it generate? Which sensors are necessary to capture the desired information? By honing in on these essential aspects, one can uncover the true potential and value of the object within the IoT landscape.
Each sensor plays a critical role in capturing specific data points. For instance, temperature sensors provide insights into environmental conditions, while motion sensors capture movement patterns. By identifying the necessary sensors and understanding the type of information they can provide, one can define the boundaries of the object’s capabilities within the IoT framework.
Conclusion
The IoT development tips we discussed here are a one-stop way of developing a flawless IoT application that will streamline your Analytics journey. An experienced IoT application development company always follows these tips to build an IoT application and lets you have crucial business insights at your fingertips.
If you are a startup looking to develop IoT applications, Finoit Technologies can be your trusted partner. With our expertise in IoT development, we offer end-to-end solutions tailored to meet your specific requirements. Our proven track record of delivering innovative and reliable IoT applications across various industries. So don’t wait to connect with our development expert.

