Planning an App? Have You Considered These 15 Application Security Best Practices?

The idea of mobile app security germinates in the code that makes the app. As David Wheeler’s Secure Programming HOWTO explains, “a good developer must be familiar with security principles and practices” to characterize the code with confidentiality, integrity, and availability.
Mobile app usage is witnessing a sharp rise as technology advances and becomes a default element of business value chains. By 2025, mobile apps are projected to represent over 50% of all digital interactions. With this increased use comes an increased risk of cyber threats, so the importance of secure coding mobile apps cannot be overstated.
The past several years have seen many setbacks in application security. The future does not seem too bright for those who do not diligently follow application security best practices. According to a report by Accenture, cybercrime is expected to cost businesses over $5.2 trillion worldwide by 2025.
These figures insist business leaders begin thinking about security early on by taking ownership. The steps would entail creating application security standards and policies under application vulnerability management, ensuring that they follow software development security best practices, and allocating a dedicated budget for app security.
In our app development journey, we have come across many companies or business owners who do not have the initial blueprint of the mobile application security best practices necessary for building secure, scalable apps.
To help companies better understand the app security requirements, we have developed a list of application security practices checklists from the perspective of business leaders, covering the vast threat landscape.
These techniques begin with understanding the mobile or web application security risks and further cover web and mobile app security best practices so that you can have more confidence in your application.
Let us first evaluate different types of application security risk touchpoints essential to address the practice of finding vulnerabilities and taking actionable measures.
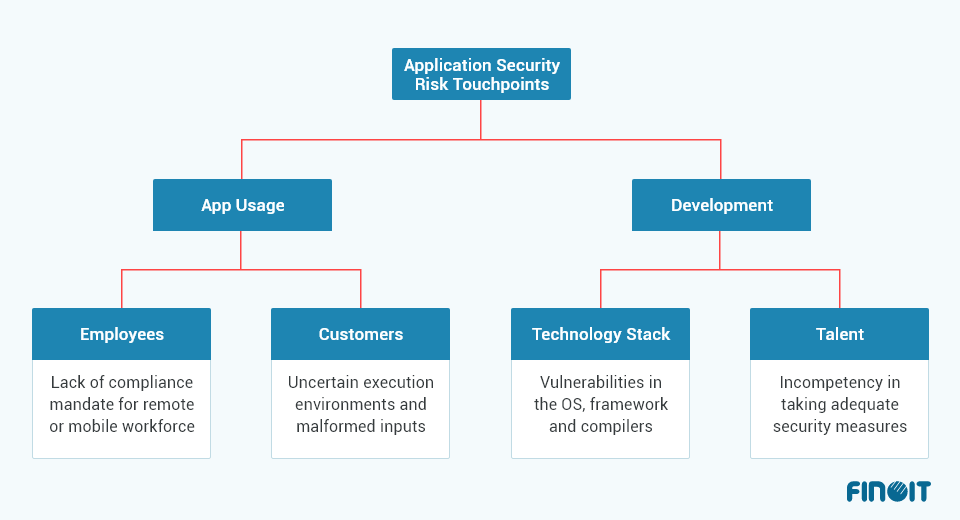
At these touchpoints, your application security is at risk. You need to identify the software vulnerabilities at these touchpoints that attackers can leverage to their advantage.
The book, The Art of Software Security Assessment-Identifying and Preventing Software Vulnerabilities defines “software vulnerabilities as specific flaws or oversights in a piece of software that allow attackers” to:
- Do malicious expose
- Alter sensitive information
- Disrupt or destroy a system
- Take control of a computer system or program
Creating a robust application security software strategy that effectively addresses vulnerabilities at all touchpoints is an important step. As a precursor, it secures the development cycle and helps combat app vulnerabilities on all the following three fronts:
- Existence: vulnerability in the application
- Access: Hackers gaining access to the vulnerability
- Exploitation: The extent of a hacker’s capability to exploit the exposure for their advantage
Gartner’s report on the app security hype cycle urges IT managers to “go beyond identifying common application development security errors and protecting against common attack techniques.” It suggests implementing standard application policy recommendations to discover vulnerabilities before hackers do.
To effectively combat application development security challenges, business leaders must thus focus their attention on these top 15 application security best practices. Implementing these practices would help them understand the threat landscape and make crucial decisions. Most of these practices are platform neutral and relevant to various app types. But before that, let’s first understand secure coding principles.
What are secure coding practices?
Secure coding practices are a set of guidelines and techniques used by developers to build software that is secure and resistant to cyber-attacks. These practices help ensure that software applications are developed with security in mind from the outset rather than being added as an afterthought.
During the development process, secure coding practices serve as principles for avoiding security flaws and help prevent, identify, and eliminate mistakes that might jeopardize the security of mobile apps.
Top secure coding practices that bolster your application security
On the app security front, you must address two key concerns; first is application vulnerabilities, and second is access control. We delve into security coding practices and guide you through the process to fortify your coding framework.
1. Track Your Application Infrastructure
According to IDG, a modern enterprise has more than 372 mission-critical applications.
A practical application security program is contingent upon many factors, such as an organization’s ability to align skills, create traction to encourage IT and security teams to take proactive measures, and optimize their security program leveraging on app security best practices.
You cannot perform all these without knowing which component of your application infrastructure is most vulnerable. Tracking application infrastructure should be the first step to creating a robust app security program. And while doing so, treat every component of the application infrastructure as unknown and insecure.
Analyze the components from the security perspective to determine what each component will require to prevent non-application components from interacting with the data you send and receive.
In your analysis, cover all the software platforms from development to runtime enablers. This step would help you determine the necessary network access controls to be implemented at the time of action so that only approved users and traffic sources can access application resources.
2. Perform Software Security Risks Assessment
Now that you have a list of the application infrastructure components, the next step is to find the security vulnerability of each element.
Through the assessment, you can create a systematic approach to determine protocols for software security policy implementation when users or systems attempt to access any component of the software infrastructure.
At this stage, you can create a strategy for a NAC system ensuring the following capabilities:
- Create policies for all operating scenarios
- Develop a policy for security compliance
- Carry out detailed profiling of all users and their devices
- Plan for guest networking access followed by guest registration, guest authentication, and guest sponsoring
- Strategize for better incidence response to block, isolate, and repair non-compliant machines
- Enable integration with multiple security and network solutions through open/RESTful API
These measures are part of both mobile and web application security best practices. It will create awareness among all your application security stakeholders to collaborate and to strengthen your network security infrastructure, warn against suspicious traffic, and prevent infection from insecure nodes.
Need Help with Mobile
App Security?
- Proven
- Transparent
- Dependable
3. Enforce Secure Coding Standards
Usually, cybercriminals leverage bugs and vulnerabilities to break into an application. They try to tamper with your code using a public copy of your software application.
To prevent the attacks, make the application tough to break through. Harden your code keeping in mind the operating system and framework vulnerabilities. While doing so, here are the factors you need to consider:
- Modules or servers that the application does not require
- Possibility for remote code execution
- Maximum script execution time
- Software language access to the filesystem
- Location of session information
- Servers, services, and software language configuration files
- Security extensions used by servers
- Incoming and outgoing traffic
- Access management
Missing any list element while coding could lead to loopholes for attackers to exploit the system.
Besides, some application security measures are specific to the programming language. Make sure to hire software developers who are aware of the application security best practices in context with particular language such as:
- Java Application Security Best Practices for Secure Coding
- OWASP Python Security
- C++ Secure Coding Standard
- PHP Security
- Ruby on Rails Security Guide
The documentation in the links is technical. As a business leader, you can go through the required measures and define the coding standards for developers or your mobile or web application development company.
4. Create App Permissions
Data sharing between two apps is one of the necessary operations performed nowadays. Data sharing activity between the apps becomes critical when un-secure permissions are used for developing the app. Utilizing signature-based licenses is nothing but an app defending itself from the firmware of another app by querying the sign-in keys’ signature.
Hence, if the data-sharing activity is processed between the two apps, the two apps must be signed in with duplicate sign-in keys. However, data sharing is directly undertaken if the two apps are already signed in with duplicate sign-in keys.
5. Limit Access to Content Providers
Content providers are the section of applications with user interfaces for the provider’s client, generally other applications, that help secure data access and communication. It have a user interface that presents app data, for an external client, in the form of data sets in tabular form. Content providers must restrict the sets of data that can be accessible by the clients.
Hence, an intelligent app developer must provide the permissions for their content providers to define what set of data is provided for the client. If no such licenses are provided, the content provider’s data can be read and written entirely, corrupting the provider’s data.
A content provider allows private access to their content and assigns signature certificates to client applications to restrict data access. Hence, when an application queries for data, it is essential that the application must have these permissions, which makes the content provider’s data secure.
6. Encrypt All Data
In today’s world, data security is a significant issue faced by businesses across industries. Data encryption provides the security of data being exchanged by the two applications. Data encryption means systematically de-structure data so that it cannot be misused even if a third party acquires it.
This concept is not new, as it has been used for ages where the messages were sent in a cryptic form that could only be deciphered by the authorized user. App developers use different data encryption techniques, but most revolve around encryption keys. There are generally two types of encryption schemes. They are:
- Symmetric Encryption: Encryption and decryption are performed using duplicate encryption keys by both communicating parties.
- Asymmetric Encryption: There are two sets of keys, one public and another private. The combination of both will work for decryption.
Data encryption has become ever so important with the onset of the data-driven world. So, it is a responsibility of every developer to encrypt all the data with more secure and advanced data encrypting and decrypting algorithms.
7. Use Libraries Cautiously
While app development is an innovative task that requires creativity to its core, scripting the backend code is tedious. The app developers rely heavily on third-party libraries and open-source repositories to accelerate the app development task.
These third-party open-source codes are not updated regularly. They can be overwritten with hidden malicious firmware, making your app vulnerable and susceptible to data theft and providing access to sensitive information.
Although there is no definite solution to this issue, a rigorous updating process of these open-source libraries and keeping track of updating of these vulnerabilities will help lower the risk.
As an app developer, placing a series of checkpoints in the code and changing the class or method name could make it difficult for attackers to access the app’s data using libraries. The use of device update system information to keep tabs on insecure communication will also help significantly.
Evaluate Your App's
Security Now
- Proven
- Transparent
- Dependable
8. Use Authorized APIs Only
APIs are generally used to streamline the app development process and bring out the recommended actions when needed. It is a known fact that slackly coded apps provide attackers with loopholes that they thrive on.
App developers tend to cache the authorization data, which helps in the easy manipulation of information. Though this makes the job of developers easier, at the same time it also creates a room to be exploited by hackers. As a result, it is recommended to use centrally authorized APIs.
9. Ensure Proper Session Handling
Session information establishes variables such as localization settings and access rights. This applies to every interaction users have with the application for a specific duration. It helps in tracking anonymous users after their first request and then use the sessions after the user is authenticated. This way, users can be identified on any subsequent appeals.
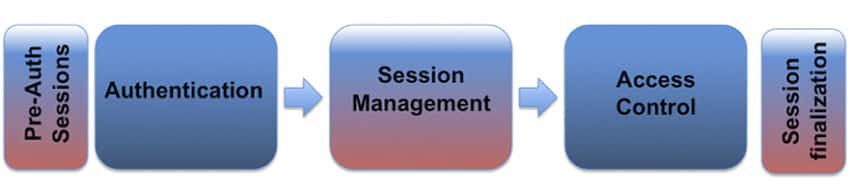
Image Source: cheatsheetseries.owasp.org
By implementing session management capabilities, you can:
- Apply security access controls
- Gain authorized access to the user’s private data
- Enhance the usability of an application
A unique Session ID or token is generated for each user to track the progress of that particular user within the application and ensure authentication. The Session ID connects user authentication credentials to HTTP traffic and authorized access controls. For secure session management, a Session ID must have the following features:
- Not have a descriptive name and unnecessary details
- Long enough so that attackers have to go through multiple ID values to identify a valid session
- Meaningless to prevent information disclosure
These features in Session ID keep it safe from disclosure, capture, brute force, or prediction, which prevent targeted or generic session hijacking
10. Store Data Safely
App development platforms provide data storage options for developers, depending on the requirements, such as the bulk of data to be stored, types of data, and accessibility. Internal storage should be the preferred option if the app contains access to sensitive data, which shall be held privately.
Adding additional encryption layers over the primary layer of encryption could help in case of any adversary or theft, as even private data is accessible.
It is not recommended to store the app data in the external or removable storage devices as when the app is deleted, the sensitive data is still saved in the external storage devices such as SD cards. The accessibility of these SD cards can be protected under such cases.
Database libraries can be used for fundamental data types and smaller data sets. The security measure in each storage option can be boosted by adding an encryption layer, which boosts data security.
11. Secure Your Containers
Docker Containers make the deployment process much easier by encapsulating a complete software package into a single portable container. The latest trend in the containerization process is to break the entire process into microservices, thus dividing the application into shared and virtualized services. Although micro-service architecture is robust and scalable, it has raised concerns about managing application security.
Here are a few measures you can take to secure your containers:
- Avoid running containers with root-level access
- Don’t store the credentials in containers instead, use environment variables
- As the default setting for containers is unprivileged, they cannot access any other devices. Usually, you have to apply the –privileged tag to allow access to all devices, but it poses a security risk. And so, checking and managing runtime privilege consistently become integral to application security best practices.
- Evaluate your security needs and consider public or private registries
- Use third-party security tools to run automated scans for proprietary and open-source vulnerabilities from start to finish, including in your registries.
You can use a range of tools, such as AWS CloudHSM, which is a cloud-based hardware security module (HSM). Use AWS Cloud, which enables you to create and use your encryption keys or Docker Content Trust if you are using Docker Hub or Shared Access Signature (SAS) if using Microsoft’s Azure.
Also, follow recognized security standards such as NIST 800-53 and Open Security Controls Assessment Language (OSCAL) standard by NIST for container security.
12. Update Your Servers
Server updates are of two types: new features and bug fixes. Commonly software engineers take great interest in new features and do not show the same level of enthusiasm for bug fixes, whereas bug fixes are more crucial updates in nature. Here is a real-life illustration of why server security is crucial and why you must keep your servers updated.
One of the best examples of how ignoring server updates can create havoc on the business is the case of Equifax, one of the largest consumer credit reporting agencies. The agency suffered a massive cyberattack in 2017, in which attackers accessed people’s names, addresses, birth dates, and social security numbers.
An investigation discovered attackers exploited a bug in the open-source Apache Struts Framework Equifax used on their online dispute web app servers. Apache software foundation was aware of the vulnerability in the platform in 2017 and has released information about it, along with an update to fix the issue, two months before the attack on Equifax.
Importance of Server Updates
Companies must use server updates, mainly bug fixes, to defend against attackers. Always refer to the documentation for your operating system or distribution else, keep a manual check to ensure timely software updates. At times, software updates create issues. Software engineers can handle it by applying the software updates in a second environment and deploying them on a live system if they succeed.
13. Perform Stringent Testing
Software application security testing forms the backbone of application security best practices. Checking for security flaws helps combat potent and prevalent threats.
Application security testing can easily detect injection flaws when an attacker sends malicious data to an interpreter, which must not be executed without authorization.
In the wake of these requirements, security testing tools have been developed into a robust market, with technology vendors offering a range of automated app security testing tools to perform the following:
- Static Testing: Code analysis at a fixed point of time during development
- Dynamic Testing: Analysis of running code. It stimulates attack on the production system and thus reveals attack patterns
- Interactive Testing: Includes elements of static and dynamic testing
- Mobile Testing: Testing in a platform-specific mobile environment
Automated testing tools are available as an on-premises or a SaaS-based subscription service. While selecting the tools, check the programming language tools support. Some tools support one or two languages; others are designed to test the code in a specific environment, such as Microsoft Dot Net.
- These days Penetration Testing is very common, wherein ethical hackers try to hack the software application to test the organization’s defense systems. Application security vendors provide ethical hacking services with the initial scope and goal-setting, learn about the target, and break into the target asset.
14. Choose Automation for Application Vulnerability Management
The growing volume of new vulnerabilities, complex environment, and evolving threat landscape make intelligent automation necessary for cyber risk reduction.
With automation, you can optimize the manual processes and repetitive steps to stay on top of patching. IT and security teams can increase the speed of information gathering and take action to implement a fix.
Leveraging automation, you can automatically implement compensating controls through your Network Access Control (NAC) systems, Endpoint Detection and Response (EDR) tools, and firewalls.
You can decide what data sources are needed to automate vulnerability discovery in different networks. You can also look for analytics-driven automation to analyze vulnerabilities considering your attack surface.
15. Stay on Top of New Standards
Avoid taking the traditional approach to application security. Today, software security is about creating a solid defense mechanism that allows you to identify the threat combination patterns and fix the issues in advance. Unlike previously, it is not the last thing you do when developing the application.
You must start creating standard policies at the very early stage of the app development process. This is only possible if you know where to implement your application’s best practices.
The best way is to follow the recommendations of standard bodies such as OWASP and the NIST. These bodies set standards for secure coding and remove misconceptions around app security.
Following OWASP’s top 10 policy for application security, you can create security assessment programs—from the idea’s inception to the development and regular maintenance and security audit.
Also, keep checking security advisories and databases such as the National Vulnerability Database (NVD), which records the vulnerabilities discovered and reported by security researchers for public consumption.
Essential elements to consider when implementing secure coding principles
The correct security tooling, changes in developers’ mindsets, and new procedures must all be adopted to implement secure coding standards. We examine each of these in detail.
Developers: Developers must be trained to understand the importance of security in coding so that the foundation for code security is set.
Workflows: Have a security framework to guard the software development lifecycle (SDLC), where the code is protected as it moves from one stage to another. Security readiness help in countering coding security issues better than adopting a reactive approach.
Tools: Developers must select tools that not only user-friendly but also bring in security to the development process. They must carry out a critical evaluation of libraries, frameworks, and technologies to ascertain security competitiveness.
Why are secure coding practices so important?
Secure coding standards are necessary and applicable to all mobile app development teams. As Alberto Bacchelli, associate professor at the University of Zurich, points out, “Studies conducted have provided evidence that developers often miss vulnerabilities during code review even though they might have had the knowledge to detect them,” speaking to The Daily Swig. As a result, secure coding practices are of immense importance to mobile app development. Noteworthy reasons that make them essential include:
Use data protection
“Developers have a responsibility to protect user data. Failure to do so can lead to serious consequences for both users and the app developer.” – Matt Cullinan, CEO of CyberGRX.
Insecure development standards can expose mobile apps to SQL injection, cross-site scripting (XSS), and other forms of data theft. For example, in 2019, the popular dating app Coffee Meets Bagel suffered a data breach that affected over 6 million users. The breach was caused by a vulnerability in a third-party library used by the app.
Safe coding practices could have prevented this vulnerability from being exploited, protecting users’ sensitive information. Therefore, safe coding standards are required to assist in the security of user data by ensuring that sensitive data is appropriately encrypted, stored, and transported.
Ward off cyber attacks
Secure coding practices protect user data and reduce the risk of cyber-attacks by preventing vulnerabilities that hackers can exploit. Mobile app developers can limit the risk of successful cyberattacks by integrating security features such as input validation, access control, and encryption to protect against typical attack vectors.
Maintaining user trust
In a survey by Edelman, 81% of respondents said that they need to be able to trust a brand to buy from it. And Apple is a successful example of user trust because of its emphasis on security and privacy, which has helped to establish it as a trusted brand. The corporation’s adoption of hardware-based encryption, secure boot, and other security measures has aided in the protection of user data and the retention of user trust.
So, it’s evident that custom mobile app development services can protect user data which can in turn, build user trust and confidence in the app’s security measures.
Easily comply with regulations
The benefit of using secure mobile app development is that it reduces legal risk. Developers use best practices such as input validation, encryption, and access controls, eliminating legal penalties, financial losses, and damage to a company’s reputation.
Compliance with regulations like GDPR, HIPAA, and PCI-DSS is also vital, and secure mobile applications help ensure that software is secure and compatible with these regulations, which is critical for organizations to maintain consumer trust and avoid hefty legal penalties.
Cost-effective development
Coding standards contribute to developing code that is simple to maintain and execute. As a result, reusing a previously developed module is conceivable, saving time and money on development. It also makes it easier to refer to code even when the developer cannot explain the function it performs.
When coding standards are set, using the code and getting the desired results becomes easier. Moreover, the means and coding style can be set according to the organization’s needs, which brings flexibility to the system.
No financial loss
In today’s digital landscape, where security is a crucial differentiator for businesses, organizations prioritize secure coding practices to protect themselves from financial losses. In addition, these practices can save an organization’s reputation, lower insurance premiums, increase competitiveness, and lead to better returns on investment.
- Protection against reputational damage: By leveraging app secure coding practices, organizations can reduce the risk of security incidents and protect their reputation.
- Lower insurance premiums: Many insurance companies offer organizations with secure coding practices lower premiums.
- Better ROI: best practices can lead to higher returns on investment by reducing the risk of security incidents and improving the quality and reliability of software.
- Increased competitiveness: Organizations with strong security practices are likelier to win business and gain a competitive advantage.
- Fulfills quality promise: Maintaining optimal coding practices results in a higher quality end product. This is, without a doubt, the most significant advantage. Setting higher standards for ourselves and keeping clients satisfied implies producing a higher-quality end product.
Support for a security-conscious culture
Promoting secure coding practices encourages development teams to adopt a security-conscious culture. Developers become more aware of potential dangers and take preventative action to mitigate them when security is included as a crucial component of the software development lifecycle.
You can consider adhering to OWASP Software Assurance Maturity Model – an open framework that will prove tremendously helpful to your developers in coding securely.
What security coding standards must be followed during mobile app development?
Developments must be aware of and implement some known security standards when developing mobile apps. They help understand security weaknesses or errors in code and vulnerabilities and help prevent such occurrences.
CWE
Common Weakness Enumeration (CWE) provides a list of software and hardware security flaws found in various programming languages, including C, C++, and Java as well as code libraries and applications. It features over 600 classifications, including subcategories for buffer overflows, path/directory tree traversal issues, race situations, cross-site scripting, hard-coded passwords, and unsafe random numbers.
NVD
The National Vulnerability Database (NVD) standard, which comes from the National Institute of Standards and Technology of the United States government, checks for data vulnerabilities. It is tied to the Common Vulnerabilities and Exposures (CVE). Additionally, it helps provide the necessary details like severity rankings, effect rankings, and methods of patching these vulnerabilities.
CERT
The most popular programming languages, including Java, C, and C++, are supported by the CERT standard. It compiles a comprehensive list of vulnerabilities and offers a risk analysis emphasizing the severe repercussions of breaking the established regulations. CERT (Computer Emergency Response Team) experts are a diverse group of researchers, security analysts, software engineers, and specialists in digital intelligence who collaborate to identify security flaws in software products, make long-term improvements to networked systems, and create state-of-the-art knowledge and training to advance cybersecurity practice.
ASVS
The Application Security Verification Standard (ASVS) embedded in OWASP secure coding provides a thorough checklist of secure coding best practices to help prevent security flaws. Using threat modeling techniques, ASVS examines the architecture and design for stored and in-transit data. it prevents malicious injection, and secures error handling, logging, and data protection for specific configurations.
DISA STIG
DISA STIGs are configuration standards developed by the Defense Information Systems Agency (DISA) to make device hardware and software as secure as possible, safeguarding the Department of Defense (DoD) IT network and systems. Compliance with STIGs is a requirement for DoD agencies or any organization that is a part of the DoD information networks (DoDIN).
Conclusion
Safe coding standards are an inescapable component of software development, and developers must stay diligent and up-to-date on the latest security threats and practices to keep their apps and users safe.
Business leaders who want to have robust and secure applications must begin to think about software security right at the beginning. The implication is that app security should influence their important decisions, such as choosing an app development company and implementing the right technology stacks.
Together with their technology partner, they should work on setting up standards and policies and blend the app security best practices well into the software development life cycle.
If you also want to build a secure mobile app, consulting with a reputable company and joining hands with Finoit Technologies can be an effective way to implement these secure coding practices. So, to get all your queries answered, connect with our development expert now.
Need Help with App
Development and Security?
- Proven
- Transparent
- Dependable


